Cybersecurity researchers from the firm Hunters discovered a vulnerability in Google Workspace that could allow unwanted access to Workspace APIs. The flaw is significant in that it could let attackers use privilege escalation to gain access that would otherwise only be available to users with Super Admin access. Hunters named this security flaw DeleFriend.
Jump to:
- Vulnerability uncovered in Google’s domain-wide delegation
- Why this Google Workspace vulnerability is particularly dangerous
- How to detect and defend against DeleFriend
- Proof-of-concept tool for running DeleFriend manually
Vulnerability uncovered in Google’s domain-wide delegation
According to the Hunters team, the vulnerability is based on Google Workspace’s role in managing user identities across Google Cloud services. Domain-wide delegation (DWD) connects identity objects from either Google Workspace Marketplace or a Google Cloud Platform Service Account to Workspace.
Domain-wide delegation can be used by attackers in two main ways: to create a new delegation after having gained access to a Super Admin privilege on the target Workspace environment through another attack, or to “enumerate successful combinations of service account keys and OAuth scopes,” Hunters said. This second way is the novel method the researchers have discovered. Yonatan Khanashvilli, threat hunting expert at Team Axon at Hunters, posted a much more detailed explanation of DeleFriend.
Response from Google
Hunters disclosed this flaw to Google in August 2023 and wrote, “Google is currently reviewing the issue with their Product team to assess potential actions based on our recommendations.”
An anonymous Google representative told The Hacker News in November 2023, “This report does not identify an underlying security issue in our products. As a best practice, we encourage users to make sure all accounts have the least amount of privilege possible (see guidance here). Doing so is key to combating these types of attacks.”
Why this Google Workspace vulnerability is particularly dangerous
Hunters said this vulnerability is particularly dangerous because it is long-term (GCP Service account keys do not have expiry dates by default), easy to hide and hard to detect. Once inside an account with Super Admin privileges, attackers could potentially view emails in Gmail, view someone’s schedule in Google Calendar or exfiltrate data from Google Drive.
“The potential consequences of malicious actors misusing domain-wide delegation are severe. Instead of affecting just a single identity, as with individual OAuth consent, exploiting DWD with existing delegation can impact every identity within the Workspace domain,” said Khanashvili in the press release.
SEE: Overworked IT pros in Australian small businesses have several options for dealing with cyber security. (TechRepublic)
How to detect and defend against DeleFriend
In addition to ensuring privileges are set up properly, as Google notes, IT admins could create each service account in a separate project if possible, Hunters said. Other recommendations from Hunters to protect against DeleFriend exploitation are:
- Limit OAuth scopes in delegations as much as possible, using the principle of least privilege.
- Avoid administrative scopes such as https://www.googleapis.com/auth/admin.
- Focus detection engineering and threat hunting practices on suspicious delegations and multiple private key creations over a short amount of time.
- Maintain security posture and hygiene best practices.
Google suggests the following:
- Please check if you are currently using domain wide delegation by visiting the Admin Console page. If you are not using DWD today then there is no current risk and future DWD usage should follow the upcoming best practices guide.
- If you have Service Accounts that you have set up for DWD, you should review each setup and secure access to those service accounts by:
- Ensuring the Service Accounts have least privileges in terms of API scopes granted to them by visiting this page on the Admin Console and revoking Service Account access to unused scopes.
- Ensure only Super Admins or equivalent security roles in GCP console have the ability to create/update those service accounts and associated keys.
Proof-of-concept tool for running DeleFriend manually
Hunters created a proof-of-concept tool for running the DeleFriend exploitation method manually. The tool works by enumerating GCP Projects using the Resource Manager API, iterating and enumerating on GCP Service account resources and project resources, and investigating specific roles and permissions from there, including extracting private key value from a privateKeyData attribute key (Figure A). The end result is a JWT object, which can be exchanged with a temporary access token to allow access to Google APIs. Konanshvili’s blog post contains more detail.
Figure A
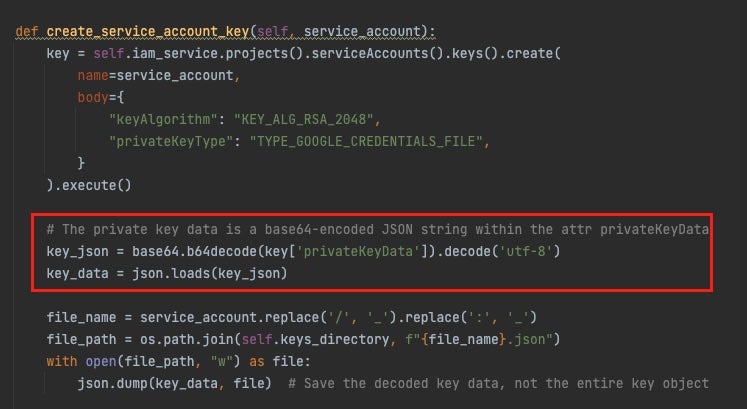
The tool is intended for researchers in order to detect misconfigurations, and “increase awareness around OAuth delegation attacks in GCP and Google Workspace and to improve the security posture of organizations that use the Domain-Wide-Delegation feature,” Hunters wrote.
Note: This story was updated with recommendations from Google.