
Hardware
SecurityHow to Use Google’s Titan Security Keys With Passkey Support
Google's updated Titan Security Keys can serve as a multifactor authenticator and store passkeys to replace passwords.
You're on page 2, See the latest articles on Hardware.

Google's updated Titan Security Keys can serve as a multifactor authenticator and store passkeys to replace passwords.

Lenovo, AMI and Insyde have released patches for LogoFAIL, an image library poisoning attack.

Now you can write on your iPad just like writing on paper using this digital stylus with a 1.2mm fine tip, tilt function and palm rejection technology.

Data storage technologies are crucial for safeguarding business info and protecting it against data loss, cyber threats and crashes. Various methods and options offer scalability and diverse features.

Amazon, IDrive, IBM, Google, NetApp and Wasabi offer some of the top enterprise data storage solutions. Explore their features and benefits, and find the right solution for your organization's needs.

The IBM Quantum System Two with IBM Quantum Heron processors is designed to push quantum-centric supercomputing forward.

Troubleshooting problems in any computer system can be a tedious process. The Windows Memory Diagnostic tool can help you by checking the memory installed in your system.

Time Machine lets Mac users easily backup their computer. In this tutorial, learn how to pick a drive and perform your backups automatically.

Black Friday deal alert! Gear up with a major discount of $230 on a refurbished 2015 MacBook Air, available now through November 27.

It’s time to stop relying on the insecure authentication protocol built into Windows. Microsoft is making it easier to switch to secure modern options.

Get this high-quality Speedy Mag Wireless Charger for iPhone while it is discounted by 70% from the original price.

The Maia and Cobalt custom chips will be available within Microsoft’s cloud infrastructure.

The strange vulnerability could have allowed for escalation of privilege, denial of service or information disclosure attacks.
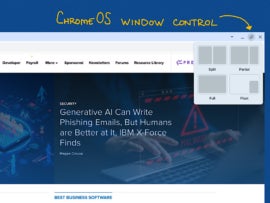
ChromeOS users, learn how to use these hidden browser window controls, and find out why you’ll want to use them.

Any company that is strategic could be targeted for the same kind of actions as this cyberattack. Follow these tips to mitigate your company’s risk to this cybersecurity threat.